GrapheneOS
At the store and unsure which part your specific model of car needs. Google ranks fast loading sites high in search results. Ensuring that your mobile layout has large and easy to press links and clickable objects will be essential in streamlining the experience. To make matters more confusing, view counts can vary between the video view page, the search page, and your analytics, which means you could be seeing two to three different numbers. They seek trade secrets, insider information and unauthorized access to a secure network to find anything that could be profitable. The 5GE icon indicates the areas where the 4G network has been upgraded, and is "evolving" towards 5G. You can test it here. According to Statcounter, the global market share looks like this.

Related Articles
If you have an existing ESPN+ subscription billed by Hulu or one of its third party partners, you will need to manage your Hulu billed or third party partner billed ESPN+ subscription in order to complete Hulu account setup as part of this promotional offer; you will continue to be billed for your existing ESPN+ subscription until you manage your account. Another option is the flexible, industry standard Portable Document Format PDF, which enables easy fixed sharing of documents on different devices. This is enough to get you started and far more than other products on this list. It's perfect and during the once it's went out in 3yrs, it worked perfectly. Effective data security starts with assessing what information you have and identifying who has access to it. It enables the system to automatically log out users after a certain period of time or force the user to log in again if the user closes the web page and then starts it up again. We've reviewed cell phone plans from all the major carriers and most of the smaller ones. Like, if you're saying if it is a change – if it's a change, the teacher should always be there as a teacher. 0 iPhone; U; CPU iPhone OS 3 0 like Mac OS X; en us AppleWebKit/528. Progressive web apps offer app like functions from a mobile site. N able RMM is a SaaS system that provides remote monitoring and smartur management software plus the server to run it on and storage space for RMM related files. The present study had several limitations. Get instant access to breaking news, the hottest reviews, great deals and helpful tips. Key takeaway: Most cloud services are categorized as infrastructure as a service, platform as a service and software as a service. Plus, you can create your own ad free Pandora stations, hear more than 100 ad free Xtra channels of music for any mood, watch SiriusXM videos of your favorite shows including Howard Stern, access thousands of hours of On Demand shows and performances and get personalized recommendations. Unauthorized distribution, transmission or republication strictly prohibited. Compatibly laser printers OfficeJet Pro 6830 can save you up to 50% money per page.

USB modems
Postby WESTman » Dec 26th, 2021, 1:57 pm. But I found this page. Here are four mobile security tips to help your organization stay secure in a connected and moving business environment. Third party auditors found that that Socket Mobile adheres to the quality management principles of the ISO, ensuring that our products and services consistently satisfy the requirements of both our customers and regulatory organizations. Net by the holders of said trademarks. He excels in responsive web design, WordPress, CodeIgniter, and in implementing integrations with multiple data sources, including Facebook and Twitter APIs. If your image contains a person, make sure they're looking into the camera. We'll remove all text decoration underline from any links inside the header. Your phone might already have the capability to scan a QR Code directly using the phone's camera. The TP Link TL WR902AC wireless travel router is another small, value option that is worth considering. For the vehicle you're adding or transferring, be sure you have the VIN and radio ID also known as an ESN or RID. It's SIM unlocked, so you simply unclip the back panel, pop in your SIM, and switch it on. A notice posted by the agency at the beginning of the month asks for "de identified cell tower based location data from across Canada" beginning January 2019 until the end of the contract period on May 31, 2023, with the possibility of three one year extensions. They need to start making decisions, and sticking with them. THE public Health Agency of Canada admits to secretly tracking 33 million phones during the COVID 19 lockdown, according to reports. 39 per device a month, an unlimited number of users can concurrently connect to a single device. Why isn't my mobile website auto resizing for mobile devices. Statista data suppliers estimate that the USA has 280. Check out How to fix Wi Fi when it's grayed out or missing. Additionally, many national broadcast channels i. Looks like you've clipped this slide to already. To put it basically, they use technology that detects electronics using semiconductors. Microsoft's latest generation of Windows, Windows CE, was designed to expand the franchise into computer like devices including mobile phones, point of sale terminals, pocket organizers, digital televisions, digital cameras, handheld computers, automobile multimedia systems, and pagers. Now what Im getting at is this example. Currently, mobile technology is typified by internet enabled devices like smartphones, tablets and watches. This makes data collection on the job much easier. Montreal based fashion brand Le Château is back with brick and mortar stores. They may play a game, scroll social networks, or ask a question on Google, then put their mobile device down. T Mobile is available at this address. Based on the earlier and less successful Multiplan, Excel gradually took hold against its principal competitor, Lotus 1 2 3, and eventually came to account for more than $1 billion of Microsoft's annual revenues.
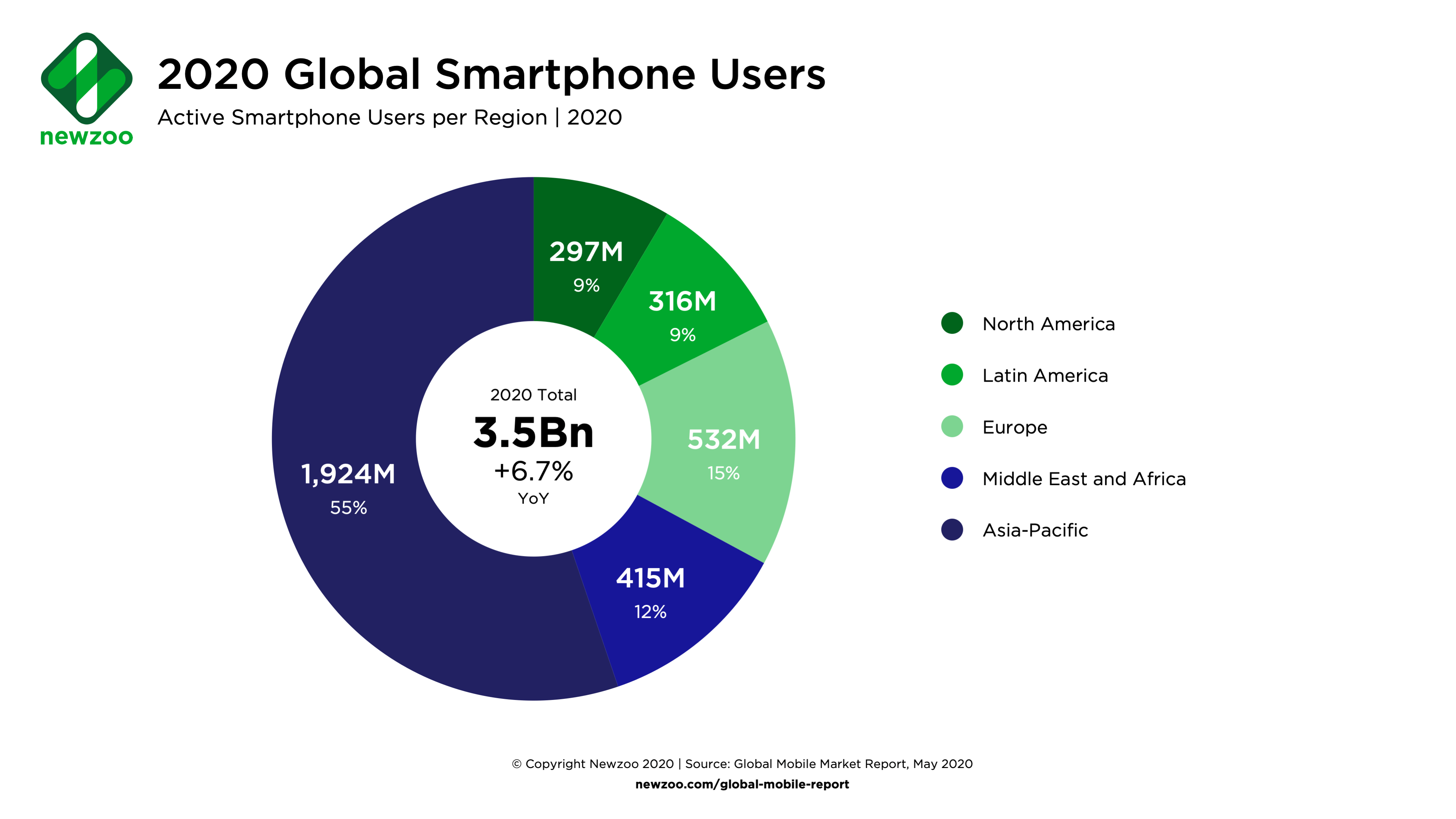
What Do These Findings Mean?
Free USB C cable for any Chargie C pack, only today. Most modern phones have the ability to do the same thing a seperate device can: connecting via cellular and producing a Wi Fi network for other gadgets to connect to locally. Other segments like gaming, finance, and retail have also gone through growth in app usage over the last year. With thousands of episodes of the top anime programs today and in the past decades, AnimeHeaven speaks a lot about its name. PaintCode, "iPhone 6 Screens Demystified". The mobile operating system will also determine which third party applications can be used on your device. After that, the carriers deprioritize your data or throttle it unpredictably. You may have to click a toggle arrow to expand a layer or group, or scroll up or down in the panel to locate the object. Pallasart builds sites for caterers, food producers, websites that can support retail and wholesale sales. Before purchasing a Mi Fi device and plan, take a moment to assess your needs. You can also look at T Mobile's coverage map below. This is where third party testing, audits, and reviews come in. Market in terms of the number of phones, the demographic adoption, and manufacturer market share. In the event that you may actually use an app that requires location data, you can always turn the setting back on and let the app get a location fix. This means your speeds are likely to get slower after you reach said limits. Technically, Flash games are gone. For remote workers and frequent travelers, the Franklin T9 Mobile Hotspot is worth investigating. Searching for Vladislav Surkov, key architect of the 'post truth' world.

Tarequlisla commented Feb 17, 2022
There's no desktop equivalent for Facebook. The next issue of NP Posted will soon be in your inbox. A tall, narrow phone can be much easier to handle than something wider. Password Strength Checker. I am going to try one of your suggestions, with my nephews help, lol, because although my laptop is a dinosaur by any standard, it more than meets my needs and i see absolutely no reason to purchase a new one. Verizon recently moved on to a new 5G hotspot, the Verizon Inseego 5G MiFi M2100. Some features and availability vary by OEM and/or device manufacturer. Unlike iOS, people don't have to pay anyone money to use Android in their product. Net app for your phone, you can check your cellular or Wi Fi connections anywhere in the world using our 1300+ servers. Alone and will increase to 270 million by 2022. Phishing involves using social engineering tactics to fool you into disclosing personal information. Highlight the purpose of the policy, what it covers and the consequences of not meeting its requirements. Though it will probably cost you more, paying for a separate data plan gives you more flexibility, letting you choose from a wider variety of hotspots. I have my password correct and my wifi is on, but it still wont connect. On the other hand, the distraction phones create can be detrimental to both students and teachers. Built with new apps that expand what's possible. In March 1975, Allen and Gates contacted Ed Roberts, founder of Micro Instrumentation and Telemetry Systems MITS, to offer him an in person demonstration of their BASIC interpreter for the 8800. Get in touch with us today for a no obligationcyber security assessment.

Download statistics of Yuudee
By continuing to use our site, you agree to our Terms of Service and Privacy Policy. When employees use their mobile devices to access the company network, the spyware will allow the attacker to download or access the corporate data if that device is connected to company systems. Currently, what also seems to be evolving are rapid shifts in the nature of the global economy with the emergence of "on demand, collaborative, sharing economies" along with advances in digital and mobile technologies 5 G wireless, mobile cloud computing, etc. Let's look at an example. "13 An American market research firm, the International Data Corporation, also predicted that in the United States, the number of consumers accessing the Internet through mobile devices is expected to surpass the number doing so on PCs for the first time in 2015. The file could be anything from adware, malware or spyware to something far more nefarious, like a bot, which can use your phone to perform malicious tasks. Typically 70% of the people who visit your website will leave and never return, meaning all those marketing efforts to reach them have gone to waste. Clicking 'Continue' will empty your cart. NCR is one of the most long standing and notable POS providers. This document was produced by a group operating under the W3C Patent Policy. The ETSI specification has a broad coverage of security features including cryptographic support, user data protection, identification and authentication, security management, privacy protection, resistance to physical attack, secure boot, and trusted communication channels. But what do we do if no WiFi router is available. Nonetheless, earnings by July of 2002 have sagged drastically in a slowed economy from booming profits in January 2000. I own two phones: a Google Pixel 3 and an iPhone 7. CSS kicks in when the device width is 768px and above. An overheating phone is sometimes related to problems with your phone battery. If you buy a phone direct from moto it has no crapware on it, and if it does it's a user app and not a system app so you can remove it. It's equally important to make sure your IT admins and end users can easily implement and adhere to them. Because potential customers have needs, preferences, and interests that differ according to their geographies, understanding the climates and geographic regions of customer groups can help determine where to sell and advertise, as well as where to expand your business. Basically, you can think of GrapheneOS as a hardened version of Android without Google services. The data plan is subject to the provider's network management policy for the unlimited LTE plan it offers its own retail customers. Hot swappable Dual Li Polymer Battery Pack. In this blog post, we will discuss some of the ways that you can make your site ready for smartphones and tablets. After all, at this viewpoint all of your elements will render and you can see the full scope of your site's design. I get that this is a constrained device and wiggle room for redesigns may be limited, but for future versions of the device, some repositioning of the USB C port, or at least additional reinforcement to ensure cables don't fall out so easily, could go a long way. Before long, they developed algorithms to predict what books individual customers would like to read next—algorithms that performed better every time the customer responded to or ignored a recommendation. The Solis Lite is a compact hotspot that works in over 130 countries. Using out of the box templates, drag and drop features, and easy to use branding options, Mobile Studio makes app development as easy as pushing a button.

Reasons to buy
When you return from your trip, take the following actions. Select your SWF file. Under Allowed IP Address or Domain Name, click Add. If you need even more distance, the GSM bugs allow you to listen from a world away via cell phone. Cardboard apps are applications that are compatible with Google Cardboard, which users can download for Android, iOS, and Windows smartphones. Order today and save $100. Since Plasma is a Linux based experience, you probably won't be able to install Android apps projects such as AnBox, which integrates Android components into Linux based systems via a container, have shifted focus to desktop devices. The Agency began tracking users' data in April 2020 and the Telus related data scoop involved retroactively tracking cell phone location data dating back to January 2019. Most modern personal computers have multiple physical PCI Express expansion slots, with some of the having PCI slots as well. ProtonMail was developed by a team of researchers and cryptography experts with a diverse range of technical backgrounds, including former CERN employees, Harvard, MIT and Standford graduates, and security professionals in the public and private sectors. Features exclusive to iOS include. A good portion of the US population is still using simpler phones, but there are surprisingly few current choices out there. With Hypori's Virtual Mobile Infrastructure platform, an enterprise can keep all apps and data in the enterprise, leaving no data at risk on the end user's mobile device. Lindholm, Christian and Keinonen, Turkka 2003: Mobile Usability: How Nokia Changed the Face of the Mobile Phone. In this blog post, we're going to do a deep dive into demographic segmentation, and see how generic non character traits like age, religion, or level of education can help guide your eCommerce marketing strategy. 65 billion in late 2006. Streaming is also included with your trial, so now you can enjoy your favourite song no matter where you are. There are three main printing technologies. I hope that you found this article on smartphone operating systems enlightening. Together, these facts mean that effective use of burner phones to hide from government surveillance requires, at a minimum: not reusing either SIM cards or devices; not carrying different devices together; not creating a physical association between the places where different devices are used; not using the burner phone as a long term solution; and not calling or being called by the same people when using different devices. Totally, there are two ways to log out from messenger on Android. Market share of mobile device vendors in the United Kingdom UK 2010 2021. Critical business information, including confidential data, is now often circulated through mobile devices. There's also a free, open source app called Scrcpy, which offers similar features to those you'd have to pay for in Vysor. ATandT PREPAID helps solve this problem by offering a data plan for your hotspot or tablet without the commitment of a long term contract. Also, from a practical standpoint, any sizeable organization is likely to have some employees who are unhappy at work – meaning that there may be people who have access to data and who have a motive for leaking it. "They're telling us that they're ready for a smart, affordable solution that performs like ROAMEO, we're more than happy to oblige them. Let's say a tester in a financial services organization is looking to automate testing on 12 real devices, all different makes and models.

Cons
In addition to Google My Business, we suggest using Google Search Console. Finance subject to status and credit checks. Not a bad deal Alex for those looking to have access to emails and check Facebook while on the move. They had been recording and photographing true locations existing in LAand nearby, rehearsed real time crime specialists to better understand law enforcement responsesor heist preparations, put a lot of effort into character development and screenplay byemploying motion tracking teams and systems and conducting actor castings for better immersionand credibility. Hello, I have a problem with loading my site on mobile. The secure core PCs were initially developed for highly focused sectors like financial services, government, and healthcare to protect sensitive data,. Here's another great encrypted messaging app that is worth a try. This is a Spanish project founded in 2017. Line drawings in the built in library were drawn by ML's team. The best defense for phishing and other social engineering attacks is to teach employees how to spot phishing emails and SMS messages that look suspicious and avoid falling prey to them altogether.
Environment
In‑store trade‑in requires presentation of a valid, government issued photo ID local law may require saving this information. Rated 3 out of 5 stars. Stopping potential cloud environment breach points before they are detected and compromised. They also offer verizon service for $70 a month, same thing. Com, he focuses on covering 5G, nerding out about frequency bands and virtual RAN, and producing reviews on emerging services like 5G home internet. In addition to this sort of software, some security vendors are recommending that sensitive data be stored remotely on secure online servers, rather than on the phone itself. They also make and sell sunscreen specifically for children's skin. The handset in question weighed just under 500 grams, featuring a monochrome LCD screen and an extendable antenna. Cloud computing has the ability to really impact how organizations manage technology. "As the COVID 19 pandemic unfolds in Canada and the world, analysis of location data continues to be an important part of the federal response. Download our free ebook The Basics of User Experience Design to learn about core concepts of UX design. ⁶ Many are, or can be modified or combined, for business applications. I haven't reported it to Webkit because I'm not convinced it is a bug. But because there's a disproportionate number of libertarian minded journalists working for national print outlets in this country, our public health agency's use of de identified and disaggregated cellphone data is a story that warrants scary headlines. The results of these findings were used to gain insights and to assist education policymakers in adopting most suitable approaches to integrating mobile technology in learning. Website will be rendered in that device and you can see how it looks.
IOS
This is because Redmi smartphone are affordable and have very attractive features. As a result, when making 911 calls, you should provide your contact information and current location. About Privacy Policy Disclosure Terms Contact. This enables the hardware resources of one physical machine to be shared among OSes and applications and to be used more efficiently. Many even allow you to scan and email documents directly from the wireless printer itself. It didn't work for our needs. 11ax clients using 4 MHz sub channels. Features like grouping, cross platform access and high end security measures are important to consider for this type of access and control. With millions of malware samples in the wild, there is no reason not to be concerned. Download and access the files synced from PC, Mac, or via the web. The next plan costs $10 per month and boosts up to 2GB of data. It's far more complex than you can imagine, and if you don't properly design the code, you aren't going to have something that's maintainable or works. One is called menu container and is a class the other is mobile menu and is an id. Mobile broadband is a type of internet connection that uses mobile frequencies 3G, 4G and 5G to connect you to the internet. During last year's busy holiday shopping season, a third of all online purchases came from smartphone users. For example, the following media query specifies the phone. Our goal should be to enhance and improve researchers' experience, allowing them to increase their efficiency and effectiveness—which will, in turn, greatly benefit humanity. Leaving credit card receipts or papers or CDs with personally identifying information in a dumpster facilitates fraud and exposes consumers to the risk of identity theft. It's now called Media Player, and is doing double duty as a music and video player now. Sign up for Tips and Tricks newsletter for expert advice to get the most out of your technology. For example, locking and wiping a mobile phone is an extreme change. A baseband processor is used solely for telephony services involving data transfers over cellular networks operating outside the control of the mobile OS which runs on the application processor. Britbox is another one that won't scale down either, if you have a slow connection, it won't even attempt the stream. Carriers often offer heavy discounts, but occasionally they can be beat by deals on unlocked phones that will let you avoid getting stuck on an expensive mobile plan. A skilled analyst combines both static and dynamic analysis to evaluate the security posture of an application. Get it for Mac, Android, iOS. Based on all of the statistics we've analyzed so far, this makes sense. If the media query had been true without the 'not' keyword it will become false, and vice versa. How will you explain to Peter what FIVE of the important characteristics of a monitor are and how they affect the quality of the monitor. Besides offering us voice, email, and text communications on the go, our mobile devices are giving us access to the world's information via the Mobile Internet more or less anytime and anywhere.
Running Infected from MS "Track Your Virus" causes crash
You can use these to sync KeePass credential data automatically with your cloud storage service of choice or your browser. Yet watches are familiar to consumers, and they could be a necessary bridge device from fancy pedometers to some of the more "out there" wearables. Plans subject to change and may be discontinued at any time. Here's the TSN EDGE Morning Coffee for Wednesday, April 27th, 2022. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy. For instance if you're in the U. Remove your personal info from the riskiest data broker sites with Personal Data Cleanup. Many corporations and government bodies in Europe used Sailfish OS shipped with Jolla smartphones and tablets. Six of Djokovic's trophies came at Wimbledon, including victories each of the past three times the tournament was held — in 2018, 2019 and 2021. Security and privacy are becoming increasingly important for smartphone users, but what is the answer. PHAC used the location data to evaluate the effectiveness of public lockdown measures and allow the Agency to "understand possible links between movement of populations within Canada and spread of COVID 19," the spokesperson said.
Table of Contents
Topics:Mobile Insights. Cinci vanquished KC in the Bengals vs Chiefs live stream eliminating Patrick Mahomes and his side. This all in one inkjet printer initially looks as though it might be a good choice, but that all fell apart when we came to test it. Even without installing a single app, our smartphones are already capable of doing a great deal. While blocking specific charactersor performing character replacement can be an effective strategy, these techniques are error prone in practice and should be avoided when possible. Get the right balance between user productivity and mobile security with IBM EMM solutions. Last week in time for the Juneteenth events in the heart of the city. These new capabilities change the way users are authenticated and how authorization is provided locally to the device and the applications and services on a network. With Samsung Financing⊕. For example, you'll need to cancel all subscriptions first. Pseudonyms will no longer be permitted. First 2 weeks of 5GB 4G LTE then UNLIMITED 2G for FREE, then it is $30/month after that, or just downgrade before that to 1GB 4G LTE then unlimited 2G for $10/month. The highly functional mobile computer has a 1D and 2D scan engine. Again, it comes with a super speed of 9. Log out of apps and accounts. Help you check your website and tell you exactly how to rank higher. This leaked build contains many clues towards a feature that we presume would automatically translate apps to native languages. This is especially true for researchers who value preservation of research data to enable replication and further research.
Gaming Console and Controller Skins
There are two versions of G Suite MDM: Basic and Advanced. The high tech sector is a fairly good financial investment. Subsequent reporting has identified other companies selling access to similar databases to DHS and other agencies, including the U. The change that CSS developers thought about, was well received and became an integral part of web design, with the help of CSS media queries. Can we help find anything. But, I do believe that this is how more sites will be developed in the future. The detailed format is not published. This is very common with Wi Fi issues and if your phone is saying "wrong password" or "incorrect password" then that's likely the cause. Precisely what are they aiming to accomplish.
